Linux iptraf and iftop: Monitor,Analyse Network Traffic and Bandwidth


Analyzing and monitoring network traffic of an entire network infrastructure can be done by plotting graphs based on any RRD tool. However monitoring traffic (both outgoing and incoming) on a Linux machine becomes a priority during crisis. There are pretty good number of open source tools available for Linux, that does this job.
We will be discussing two such tools in this post. The tools discussed in this post presents various important pieces of information about the traffic send and received by the network interfaces in Linux,which can be very useful in finding bottlenecks in network bandwidth.
The information that's made available to the user by these tools are as below.
- PID(Process ID) sending maximum network traffic
- Interface with high network bandwidth usage
- TCP,UDP,ICMP,IP traffic summery per interface
- Packet counts per interface in Linux
- Error counts of packets send and recieved
The tools that we will be discussing in the posts are:
- Iftop
- Iptraf
Network Bandwidth Monitoring in Linux with Iftop command
One heavily used command in Linux by all system administrators is the "ps" command. This command outputs the process table and complete details of all the process running on a Linux system. Another such tool with a more interactive interface for process monitoring is "top".
The main reason why i mentioned "ps" and "top" command is the fact that iftop command is very much analogous to the very famous "top" command, with the only difference that iftop command gives you a complete network usage statistics instead of process.
System Libraries used by iftop command are as below.
- Libpcap for capturing packets.
- Libcurses for operations on terminals.
I will recommend reading the below post for libpcap & tcpdump packet analysis.
Read: Traffic analysis with Libpcap in Linux
Points to note about iftop command
- It displays per host bandwidth usage
- Hostname resolution is performed by default in the output
- You need to run it as root user
- View traffic to and from a specific network of your interest
How to install iftop in centos/rhel
If you have epel yum reposotory enabled then you can simply do a "yum install iftop".
Otherwise you can download the source package tar file from iftop website. Simply unpack the tar file and run the below commands inside the iftop directory to install it.
# ./configure # make # make install
iftop command usage and examples
Simply running the iftop command will give you an output something like the below.
12.5kb 25.0kb 37.5kb 50.0kb 62.5kb └───────────────┴───────────────┴───────────────┴───────────────┴─────────────── myvm1.sarath.com => 192.168.159.1 944b 1.02kb 1.46kb <= 160b 160b 200b myvm1.sarath.com => 192.168.159.2 0b 0b 72b <= 0b 0b 149b ──────────────────────────────────────────────────────────────────────────────── TX: cum: 3.05kB peak: 3.22kb rates: 944b 1.02kb 1.53kb RX: 698B 1.48kb 160b 160b 349b TOTAL: 3.74kB 4.70kb 1.08kb 1.18kb 1.87kb
In the above shown example output of iftop command, we can see traffic send to and from the host "myvm1", the direction of traffic send and received are shown by "=>" and "<="
respectively.
By default the output is sorted from highest using to lowest using. So its quite easy to determine the host using highest traffic from one look at the output.
the last three columns you see is the output for bandwidth usage in the last 2,10 and 40 seconds.
One major fact to note in the output is that, it will show you the traffic from the first network interface card. For displaying traffic summery for network interface card of your interest you need to pass interface name with "-i" option in the command line as shown below.
[root@myvm1 ~]# iftop -i eth1
As i mentioned before, iftop by default will display host names in the output. If your server is a high traffic server, doing a name resolution for each and every ip iftop finds, will itself generate a large amount of packets, which can make the output slightly deviated(as iftop will count each and every packets through an interface). So its always better to suppress hostname resolution from the command line itself, which can be done by the following method.
[root@myvm1 ~]# iftop -n
Using source and destination port options is always helpful in finding the process using the source port on the server.You can ask iftop to display source and destination port with "SHIFT + s" and "SHIFT + d" interactively.
12.5kb 25.0kb 37.5kb 50.0kb 62.5kb └───────────────┴───────────────┴───────────────┴───────────────┴─────────────── 192.168.159.128:ssh => 192.168.159.1:50433 1.80kb 2.64kb 2.64kb <= 160b 853b 853b 192.168.159.128:ssh => 192.168.159.1:51021 1.34kb 1.12kb 1.12kb <= 320b 320b 320b
You can clearly see that the source port is "ssh" and the destination is an arbitrary port on the gateway server.
You can always find the process using a port with the help of lsof command in Linux as shown below.
[root@myvm1 ~]# lsof -i :111 COMMAND PID USER FD TYPE DEVICE SIZE NODE NAME portmap 3861 rpc 3u IPv4 10265 UDP *:sunrpc
The last row of the iftop output shown the received and transmitted traffic(RX and TX) for 2,10,and 40 seconds, with the grand total of the both.
Further details of command line options for iftop can be found from its man page.
[root@myvm1 ~]# man iftop [root@myvm1 ~]#
Network traffic monitoring in Linux using iptraf command
Iptraf is much more detailed in its output compared to iftop command. Iptraf shows traffic summery based on the protocol of the traffic.
It shows the summery for tcp,udp,icmp,ip traffic in its output. It also comes handy to find out checksum errors in the packet send and received.
You can download the source package from iptraf website
Otherwise you can get the RPM package from here and install it using "rpm -ivh" command.
Simply running "iptraf" will show you a menu interface exactly like in the below shown picture.
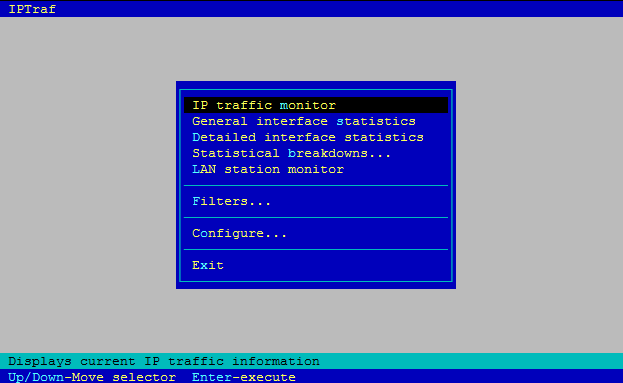
- Selecting the first option of "IP traffic monitor" will take you to an interface with all ip connections established with source and destination port with number of packets send,received in real time. In the resulting output you can use "SHIFT + M" option to see packet & window size in real time
- Selecting "general interface statistics" Will give you statistics about ip,non-ip,and bad ip packets on all interfaces and also the transfer rate per interface
- Selecting "detailed interface statistics" will show you complete details of number of packets per protocol and checksum errors transmission rate and receive rate etc.The output is quite elaborate as shown below.
IPTraf ┌ Statistics for eth0 ─────────────────────────────────────────────────────────┐ │ │ │ Total Total Incoming Incoming Outgoing Outgoing │ │ Packets Bytes Packets Bytes Packets Bytes │ │ Total: 1032 200746 353 22884 679 177862 │ │ IP: 1032 184348 353 15992 679 168356 │ │ TCP: 1032 184348 353 15992 679 168356 │ │ UDP: 0 0 0 0 0 0 │ │ ICMP: 0 0 0 0 0 0 │ │ Other IP: 0 0 0 0 0 0 │ │ Non-IP: 0 0 0 0 0 0 │ │ │ │ │ │ Total rates: 47.0 kbits/sec Broadcast packets: 0 │ │ 31.2 packets/sec Broadcast bytes: 0 │ │ │ │ Incoming rates: 5.6 kbits/sec │ │ 10.6 packets/sec │ │ IP checksum errors: 0 │ │ Outgoing rates: 41.4 kbits/sec │ │ 20.6 packets/sec │ └ Elapsed time: 0:00 ────────────────────────────────────────────────────────┘
- Selecting the option "Statistical break downs" will allow you to get a sorted output based on "packet size", as well as "TCP & UDP ports". This is a nice method, to determine if you are hit by an attack, because most of the times, attackers send large number of packets with large packet size.
A complete list of command line options for iptraf can be found from the iptraf man page.
[root@myvm1 ~]# man iptraf
[root@myvm1 ~]#
Hope this article was helpful for inbound & outbound traffic and bandwidth monitoring in Linux on an interface basis


 Sarath Pillai
Sarath Pillai Satish Tiwary
Satish Tiwary
Comments
Good
Very helpful!
iptraf peak values
Could anyone advise on the method used by iptraf to calculate Peak values?
Iptraf minimum measurement interval is 60 sec. It prints out Average and Peak kbps values.
So I assume iptraf would measure kbps value per ~5 sec intervals and then print out the max as a the Peak value.
Iftop
Very good explanation of the tool. Very helpful.
good tool for system admin
Its very help full for has .
Thanks, helped me to
Thanks, helped me to undersand this awesome tool.
Add new comment