What is MAC(Message Authentication Codes)


whenever security in communication is discussed, three things that come to mind is authentication,integrity, and data encryption. Although encryption and authentication are the major topics that needs to be taken care of, integrity of the data transferred also needs a major attention.
What problems are addressed with the help of integrity check?. Imagine that you are communicating with your friend through a chat client. How will your friend's machine know that the message he received is exactly the same message that you send?. And how will he verify that the message was not altered in the middle.
Even after implementing a secure authentication and data encryption, integrity of the message needs to be versified, to confirm, that the data was not tampered in the middle.
How to check integrity in secure communication?
In communication everything send over wire is data. So the thing that will give the sender and the receiver the assurance, of untampered data is also a small fixed length data called MAC(Message authentication code).
This small fixed length data code, that provides the assurance, will verify both accidental & intentional modification of data received.
How to generate a MAC(Message Authentication Code)?
Hash function is one of the method, that can be used to generate a message authentication code.
This is done with the help of a generating a hash value of secret key & and a message to be authenticated.
 The message to be authenticated, can be of any length. But the output of the hash function done on the message, will be of fixed length.
The message to be authenticated, can be of any length. But the output of the hash function done on the message, will be of fixed length.
this generated MAC, will also confirm the authenticity, because only the person that has the secret key can open that MAC value for verifying the data(as mentioned before the MAC is generated with the secret key value).
 As mentioned, the sender and the receiver will negotiate a secret key, before beginning the communication. This is similar to symmetric encryption, where same keys are used to decrypt at both the ends.
As mentioned, the sender and the receiver will negotiate a secret key, before beginning the communication. This is similar to symmetric encryption, where same keys are used to decrypt at both the ends.
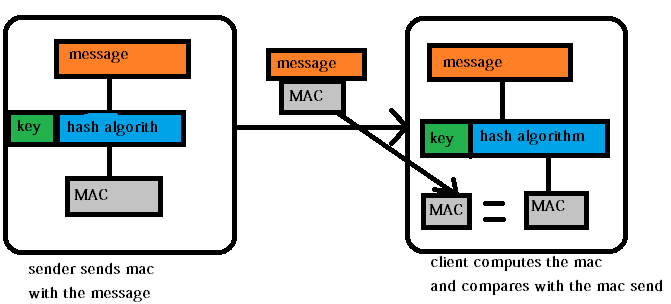
As shown in the above example, a sender will send the message, along with the MAC computed with the help of hashing algorithm's, which will be locked with the help of a secret key(which will be shared in the beginning).
And the client on receiving the message & the MAC, will recompute the mac once again, and compare, with the mac send by the sender. If the computed MAC and the MAC send, matches, the message is authenticated(because it was locked with the key previously shared) and also integrity is checked.
What are hash functions?
Let me begin this by saying that "Encryption is not everything". Because as discussed previously, encryption does not guarantee, the integrity of the message.
 The method, of transforming a message of any length, to a code of fixed length is called as a hash function.
The method, of transforming a message of any length, to a code of fixed length is called as a hash function.
 They are also sometimes called, a message digest or fingerprint.
They are also sometimes called, a message digest or fingerprint.
Hash functions are used for the below things.
- Message and data integrity
- authentication purposes
- Digital Signatures
Some points to note about hash functions
For a hash function or algorithm, it should be very easy to generate,a hash value for a given message. But it must be impossible to generate the original message from the hash value.
No two message, or data should have the same hash value, this property is called as collision resistance.
the hash function with a high collision resistance is considered to be a good hash function. Which means, the probability of two hash values being the same, will be very less.
some examples of widely used hash functions?
Secure Hash Algorithm: There are four versions of this hash functions, they are mentioned below.
- SHA-0 , this version did not last long in the field, due to major flaws in the algorithm, and was shortly replaced,
- SHA-1, National security Agency(also the people who designed SElinux), came up with SHA-1 hash algorithm. Although its similar to the famous MD5, there are differences between them. its a 160 bit hash function. SSH version 2, uses this SHA-1 algorithms for MAC.
- SHA-2 is the brainchild of National Security Agency. Its available in two versions, called SHA-256 & SHA-512.
- SHA-3 or Keccak, this hash function was the winner of the hash function competition in 2012, conducted by National Institute of Standards and Technology.
This is a pretty old hash function, which was designed in 1991. Its widely used even today, to check the message integrity. SSH version 1 used this for message integrity checks.
its a 128 hash function. the collision resistance of md5 is not good, due to which, its not used for high security implementations.


 Sarath Pillai
Sarath Pillai Satish Tiwary
Satish Tiwary
Comments
good one .....
good article bro !!!! simple and explanatory ... keep up the work :)
-cheers
sir...
thankyou
Very good
And very clear!, the best on the internet.
Secret key Means which one DH?
Here you mentioned Secret key Means which one DH(Diffie–Hellman)Key?
very good article with simple
very good article with simple and clear explanation
Add new comment